In the dawn of computing, passwords seemed to provide sufficiently strong identity validation. I have to think that people felt like some sort of secret agent typing in this string that only they know to identify themselves to a computer. These were times when cell phones were not nearly as prevalent, multi-factor authentication was expensive and proprietary, biometric technology was expensive and not natively integrated into our operating system, and CPU and memory were very limited resources on a computer.
Fast forward to today – a time when the idea of a person not having a smartphone brings to mind an aboriginal tribesman. Users of modern computers typically get concerned when CPU or memory exceed 50% of the system’s available resources and even your phone has multiple processors. We are undeniably connected to the Internet in various ways at all times, from our laptops to our phones to even our watches. Multi-factor authentication opportunities are everywhere, yet so few services harvest its capabilities.
Additionally, we have multiple services that will perform multi-factor authentication on our behalf. Microsoft, Google, and Facebook all provide strong authentication services which are completely handled on our behalf. All of those stories of a company being hacked and leaking thousands of user name and password combinations online can be a thing of the past if your service doesn’t have its own set of credentials. For those organizations which are concerned that one of these companies will get hacked I have to ask – do you think you have more invested in information security than them?
For now, let’s put federation, multi-factor, biometric, and other forms of authentication aside and take a look at the risks associated with simple password authentication systems.
Passwords are easily obtained
The simplicity of obtaining a password is nothing new to an information security professional. During assessments of customer enterprises, we’ve seen passwords stored in files, in the description field of service accounts (which everyone can read), even indexed and cached by search appliances which were given a user account with domain admin membership.
Another consideration when using password authentication is what I like to call getting “pwned by proxy”. There are numerous cases where the password to your organization is used elsewhere. Do your users utilize a different password online than they do for your business? Chances are, it is highly similar if not the same. This means that a compromise of any service which shares the same (or a highly similar) password can result in compromise of your service, and there are so many ways to find them. In this condition, you will likely never know what “patient zero” was.
How about business partners? If your organization relies solely on a password to identify users, what happens when one of your business partners gets hacked and has valid credentials to your network in their system? Again, we are left in a position where your organization may never find “patient zero”.
Passwords rely on the infallibility of human decision (which doesn’t exist)
Password authentication is only as secure as your most susceptible user’s decision-making ability. In other words, if I can trick any user in your organization to send their password over e-mail, type it into a fake web form, or provide it over the phone I can effectively steal that credential. Not all credential theft involves technology!
Phishing has plagued corporations for years, and will likely continue to be a problem as long as password authentication is in use. Even your most skilled information security professionals have clicked a link or logged on at least once, then shortly after questioned whether the page they just logged on to was legitimate (I know I have). Now imagine the non-technophile audience in your company – would they have thought twice?
Passwords can be guessed and brute forced
Most passwords are predictable. Dictionary attacks work, that’s why they’re still used today. As humans, we are programmed to use language when coming up with passwords or passphrases. Where actual words aren’t used, common keyboard patterns such as “qwerty” or “1qaz2wsx” prevail.
Using password complexity? Still guessable. Many organizations with password complexity cause users to perform simple character substitutions, capitalize the first letter, and usually utilize highly predicable patterns. In fact, if we reference a 2015 report by Trustwave we can see some of these highly complex passwords in our list of the top 10 most common enterprise passwords.
Passwords Have a Long Validity Period
Let’s compare a password to asymmetric authentication, such as certificates. One of the rules when deciding on the size of the key used for a certificate is estimating how long it would take an attacker to deduce the corresponding key pair and ensuring that the key’s validity does not extend beyond that period.
If we apply the aforementioned principle to a password (or any other form of symmetric authentication) we can state that a credential should not be guessable within its validity period. Combine that with password lockout policies and we can state that a password used for an account should not be able to be guessed in the number of attempts that could be made (without account lockout) during its validity period.
Many organizations implement a 90 day password change policy, thus we’ll use that as our password validity period. Although not a default configuration, some organizations implement policy that enforce account lockout for 30 minutes after 5 failed authentication attempts and a 30 minute period before the lockout counter is reset. Let’s do the math!
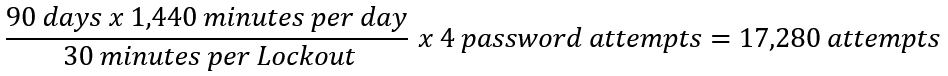
In this condition, the strength of every password on the network should be able to survive a minimum of 17,280 password attempts. Now, let’s take into consideration a password spray attack.
Password spray attacks are when an attacker uses a small number of passwords against a large number of accounts to avoid detection and lockout. Using this technique allows an attacker to stealthily scan an enterprise for its weakest accounts. For this next exercise, we will assume the aforementioned enterprise contains 50,000 user accounts.
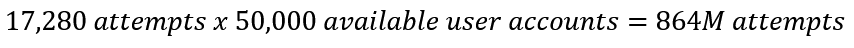
Surely, at least one password is going to fail within 864 million attempts.
…but I use a password manager with random passwords
Well, you’re better than most I suppose. This may provide some decent strength in your authentication method, but will still do effectively nothing against malware running in your user session, fake logon pages, and keylogging. Additionally, remember that the security of all of your credentials are now entrusted to that third party and their software.
While we are discussing applications used in the context of a user’s session, let’s go back to keylogging and nefarious means of gathering credentials. In many cases, keystrokes can be logged without attaining administrative authorization to the operating system – they’re usually just limited to the infected user’s session. Think about it – can your application read input from the keyboard? Then why not a keylogger.
So how do we solve this?
It is time for passwords to be replaced by a more modern form of authentication, such as biometric or multi-factor. Passwords can be used locally, but they should not be used to authenticate to remote resources.
For example, people who use Windows Hello authentication can use a PIN to safely sign into their laptop, then enable the laptop to subsequently authenticate them to networked resources with passport authentication. This means that an attacker would not only need your password, but also access to your laptop in order to trigger a successful authentication.
Other examples include using one of the previously mentioned federated authentication providers that allow for multi-factor authentication. These systems typically use a phone app or text message to validate a user’s identity. Although not infallible, this method is significantly stronger than a simple password.
Enterprise customers can use services such as Azure Multi-Factor Authentication to simplify two factor authentication deployment. This service enables two-factor authentication for Remote Desktop Protocol (RDP), Microsoft Internet Information Services (IIS), and VPN.